
(Photograph by TIMOTHY A. CLARY/AFP by way of Getty Photographs)
New York Mayor Eric Adams faces a five-count indictment that boils right down to a bribery scheme involving unlawful overseas donations. As this Supreme Court docket has made fairly clear that it doesn’t suppose most bribery is a criminal offense, Adams and his high-powered legal professionals are leaning into recasting all these funds as harmless gratuities from Turkey for good authorities service rendered.
And by “good authorities service rendered” we imply “waiving hearth codes.”
The allegations within the indictment embody particular references to a dizzying array of incriminating messages grabbed from telephones seized from the mayor and his crew. Making the entire affair a useful reminder that some — if not most — persons are very, very silly about their telephones. Or what they suppose they’ve deleted or in any other case saved hidden on their telephones.
That’s a giant deal for everybody who isn’t silly. As a result of telephones are more and more taking on as our discoverable proof repositories. And forensics professional David Greetham of Degree Authorized sees this transition from paper to laptop to telephone as the first vector of proof as accelerating. “Final yr, it was 52% of cell gadgets — the primary time it had been greater than half — and to date this yr we’re at 64%,” he mentioned.
Whether or not it’s a prison conspiracy leaving a evident digital paper path or civil litigants creating themselves a nightmare discovery downside, let’s take into account a couple of of the ridiculous knowledge assortment points concerned on this case.
Do Not Passcode, Do Acquire A number of Million {Dollars}
When Adams handed over his private cellphone to the FBI, he informed them it was locked as a result of he’d forgotten the passcode as a result of he’d not too long ago modified it to shield the proof from his employees probably deleting it.
ADAMS claimed that after he discovered concerning the investigation into his conduct, he modified the password on November 5, 2024, and elevated the complexity of his password from 4 digits to 6. ADAMS had executed this, he claimed, to stop members of his employees from inadvertently or deliberately deleting the contents of his telephone as a result of, in line with ADAMS, he wished to protect the contents of his telephone because of the investigation.
How conscientious of him!
Word that he additionally doesn’t have his telephone set as much as open by means of facial recognition, complicating the method since forcing somebody to open their telephone by means of facial recognition avoids a variety of Fifth Modification self-incrimination points if it’s non-testimonial. Certainly that is coincidence.
Thus far, the federal government hasn’t cracked the code but.
Toilet Break To Do A Quantity 3 (Delete Incriminating Proof)
Among the many extra comical episodes included within the indictment concerned an Adams staffer who allegedly confirmed as much as chat with the federal government after which tried to take a fast break to shed some potential proof
The Adams Staffer additionally agreed to talk with FBI brokers and falsely denied the prison conduct of herself and ADAMS, amongst others. At one level throughout her voluntary interview, the Adams Staffer excused herself to a rest room and, whereas there, deleted the encrypted messaging purposes she had used to speak with ADAMS, the Promoter, the Turkish Official, the Airline Supervisor, and others.
When you’re speaking to the FBI… they already know concerning the messaging apps.
Nevertheless it’s much more futile than that. Greetham defined that individuals don’t appear to know that eradicating the app from the telephone is just about ineffective.
I feel what folks neglect is that, should you destroy your telephone, otherwise you neglect your passcode, otherwise you improve your telephone, the messaging apps survive that. Messaging apps like Sign, Telegram, Snapchat, ephemeral messaging — you possibly can go online on a special telephone. It’s not constructed into the OS in the identical method SMS or iMessage for iPhone is.
And even iMessage messages may be recoverable by means of iCloud if the consumer employs that system.
Even with out moving into the consumer’s account by means of one other system, an FBI doc uncovered by a FOIA request a couple of years in the past instructed that the federal government might have restricted entry to info on these encrypted companies already.
However the ethical of the story is that eradicating the app as a cute icon on the telephone will not be doing a lot to clear that proof.
It is going to go a good distance towards making you appear to be you’re engaged in spoliation usually although!
Gone However Not Forgotten
As well as, in March 2019, whereas exchanging textual content messages to plan one other doable to journey to Turkey wherein the Airline Supervisor would prepare journey for ADAMS, the Adams Staffer texted ADAMS, “To be o[n the] protected facet Please Delete all messages you ship me.” ADAMS responded, “At all times do.”
Pobody’s nerfect!
Sadly, that is a type of strikes the place 99 p.c nonetheless isn’t sufficient. As a result of the existence of even one message like this units up the prosecutor or adversary counsel to hunt unfavourable inferences and it units up a forensics professional to do some extra digging. Greetham in contrast it to a scenario that “occurs greater than you suppose,” the place a pc might seem clear however “you verify some web historical past, and also you’d discover the current search phrases had been, ‘how do I delete knowledge with out being caught?’”
But when Adams actually meant “USUALLY do.” It turns on the market are nonetheless methods to probably get better deleted messages. However there’s a price. Greetham explains:
In instances the place you want deleted messages, you’re taking extra of full forensic picture just like the previous method of doing laptops and desktops. The draw back to that’s that the iOS updates that come out very often have added safety each time [ed. note: we were using the example of an iPhone, but the issue is similar for other phones]. And with the present iOS model, the one identified method to do this is to jailbreak the telephone. And technically jailbreaking the telephone is altering the proof.
That mentioned, “altering the proof” on this method isn’t the tip of the world. There are procedures for authenticating the outcomes involving witnesses supervising the undertaking that may affirm that nothing within the course of compromised the finally related knowledge. Nevertheless it’s an extra consideration to judge earlier than rooting round in a telephone searching for deleted messages nonetheless buried within the database.
After all, possibly the federal government received’t have to get all the way in which into the deleted messages…
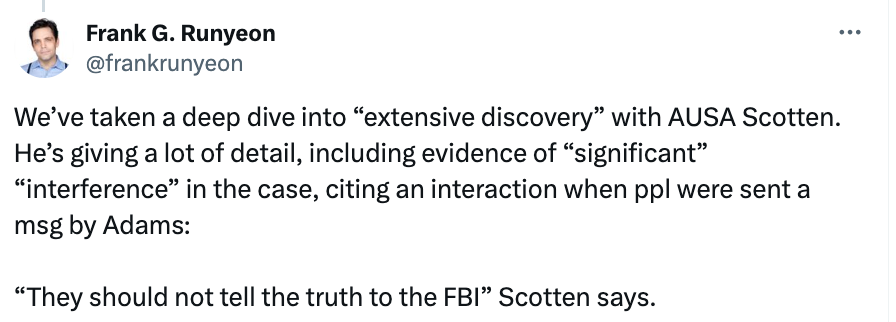
Some persons are very silly about their telephones. It’s doable that some persons are simply very silly usually.
Earlier: Eric Adams Argues That Turkish Delights Slipped Into His Pasties Had been Ideas, Not Bribes
 Joe Patrice is a senior editor at Above the Regulation and co-host of Pondering Like A Lawyer. Be at liberty to e-mail any ideas, questions, or feedback. Observe him on Twitter or Bluesky should you’re excited about regulation, politics, and a wholesome dose of faculty sports activities information. Joe additionally serves as a Managing Director at RPN Govt Search.
Joe Patrice is a senior editor at Above the Regulation and co-host of Pondering Like A Lawyer. Be at liberty to e-mail any ideas, questions, or feedback. Observe him on Twitter or Bluesky should you’re excited about regulation, politics, and a wholesome dose of faculty sports activities information. Joe additionally serves as a Managing Director at RPN Govt Search.
